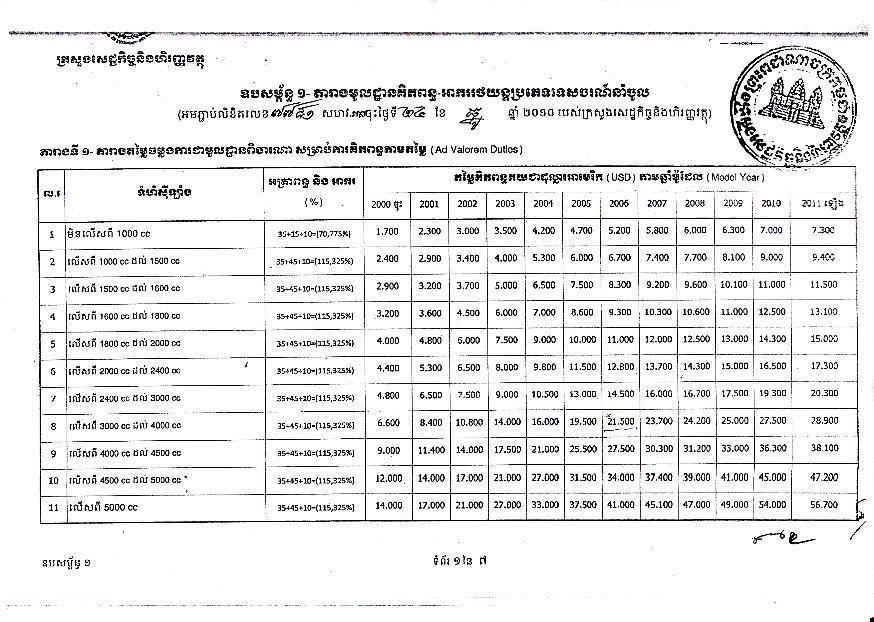
Chryslers can be hacked over the Internet
Hackers can cut the brakes, shut down the engine, drive it off the road, or make all the electronics go haywire.
Jeep Cherokees, Chrysler 200s, Dodge Rams, and several other vehicles are vulnerable to such attacks, according to research exposed Tuesday.
The core problem? A flaw in the wireless service Uconnect that connects these cars to the Sprint cellphone network.
The researchers, Charlie Miller and Chris Valasek, very first demonstrated the hack to Wired Magazine by remotely hijacking a Jeep Cherokee driven by a news reporter.
“Right now I could do that to every [Chrysler] car in the United States on the Sprint network,” Miller told CNNMoney on Tuesday.
The researchers have concluded that the vulnerable Chrysler models are those from late 2013, all of two thousand fourteen and early two thousand fifteen that are loaded with Uconnect and the utter navigation displays.
But Miller said there could be other vehicles with this weakness that he isn’t aware of. The researchers did not test any cars made by Ford, General Motors or others — but only because they’re a lil’ team that lacks the funding to keep buying cars and the time to break into them.
Chrysler acknowledged the problem to CNNMoney on Tuesday. Chrysler said it left an unused computer communication channel open that unknowingly granted outside access to car controls. It is now suggesting a software upgrade that it says customers should install “at their earliest convenience.”
But Chrysler didn’t refer to this as a recall — or say drivers are at risk.
“Similar to a smartphone or tablet, vehicle software can require updates for improved security protection,” the company said.
Miller and Valasek said they introduced their research to Chrysler last October, permitting the company develop a fix. Miller said the company had been “very kind and responsive.”
Explaining the hack
Modern day cars are smartphones on wheels – and just like any computer, vulnerable to hackers. As CNNMoney has investigated in the past, the computers inwards cars are still pretty “dumb.”
In 2013, Miller and Valasek demonstrated how they could hack a car while sitting inwards it. At the time, they had to physically connect a laptop to a car’s dashboard.
Wireless connectivity — now standard in almost every car — has upped the risk.
In this latest experiment, Miller and Valasek used a laptop to scan for any cars on the Sprint network that also use Uconnect.
In seconds, these researchers can tap into any car’s “infotainment system.” They can turn off the air conditioner, blast the radio volume, and switch the navigation screen.
Once inwards, they can then penetrate what’s supposed to be a guarded layer: the computer backbone of the car. They can control the brakes, steering wheel and accelerator.
In the past, auto suppliers and car makers have assured CNNMoney this crossover — from infotainment to core controls — was unlikely.
The researchers noted that Sprint ( S ) , as the network operator, is also in the position to block this kind of attack. Sprint did not tell CNNMoney whether it would do that on its own, but the company said it is “working with Chrysler to help them secure their vehicles.”
What’s next? On Tuesday, two U.S. senators introduced legislation to establish national safety and privacy standards for automobiles — and a rating system that tells you how safe a car is from cyberattacks.
Senators Edward Markey, of Massachusetts, and Richard Blumenthal, of Connecticut, call it the Security and Privacy in Your Car Act.
Next month, Miller and Valasek will expose exactly how they hacked into the infotainment system, tho’ not how they hijacked car controls.
Miller noted that it took him and his acquaintance almost a year to figure this out. That should keep your average punk from figuring out how to do this — but only for a brief while.
“It shouldn’t be possible,” Miller said. “I’m frightened because you should not be able to attack cars remotely like this.”